Step 1 | Get started with SSO
Single Sign-On (SSO) lets people sign in to your Base44 app using an external identity provider that supports OpenID Connect (OIDC), such as Google, Microsoft, GitHub, Okta, Apple, or Kakao, instead of creating a separate login for your app.Notes:
- Single sign-on (SSO) is available for Base44 apps on the Elite plan or higher.
- To connect a provider such as Kakao through SSO, you need your own account with that provider and an app configured there. You are responsible for creating and managing the client ID, client secret, redirect URI, and any other credentials in your identity provider’s dashboard.
- Go to your app editor in Base44.
-
Check your browser’s address bar and find the app ID between
/apps/and/editor/in the URL. -
Build your redirect URI by replacing
{{APP_ID}}in this format with your app ID: https://app.base44.com/api/apps/{{APP_ID}}/auth/sso/callback
Example: From app URL to redirect URI
Example: From app URL to redirect URI
With the app editor open, the URL might look like this:https://app.base44.com/apps/686404784ac37377589a1f7f/editor/…Here, 686404784ac37377589a1f7f is the app ID. Plug that into the format:https://app.base44.com/api/apps/686404784ac37377589a1f7f/auth/sso/callbackThis is the redirect URI you’ll enter with your SSO provider.
Step 2 | Choose your provider
Start by choosing the identity provider your team already uses. You can pick a built-in option (Google, Microsoft, GitHub, or Okta), or use Advanced / Manual configuration to connect any OIDC provider, including Kakao, or your own IdP.Google Workspace
Allow sign-in with Google Workspace accounts.
Microsoft 365 / Entra ID
Allow sign-in with Microsoft 365 or Entra ID.
GitHub
Allow sign-in with GitHub accounts.
Okta
Allow sign-in with your Okta directory.
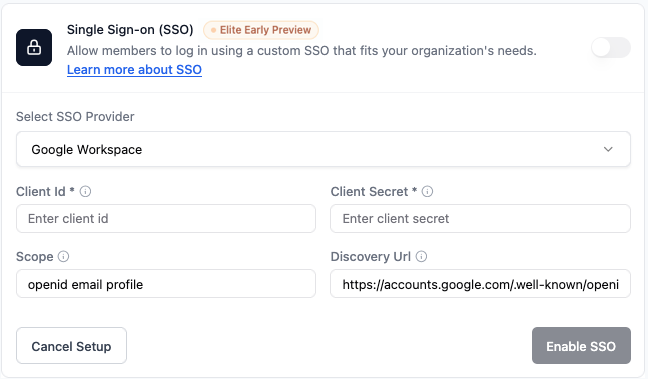
Google Workspace
Use Google Workspace as your SSO provider with an OAuth 2.0 Web application. First, create an OAuth 2.0 client in Google Cloud Console for your project, then add those credentials in Base44. To set up Google Workspace SSO in Base44:- In your app editor, click Dashboard.
- Click Settings.
- Click Authentication.
- Click Set Up next to Single sign-on (SSO).
- In Select SSO provider, choose Google Workspace.
- Enter your Client Id and Client Secret from Google.
- Keep Scope as
openid email profile. - Leave Discovery Url set to the default value.
- Click Enable SSO.
Microsoft
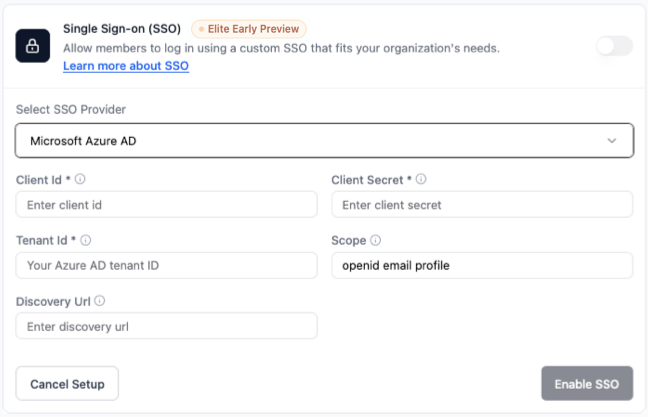
Use Microsoft Entra ID (Azure AD) as your SSO provider through your Azure portal. To set up Microsoft SSO in Base44:- In your app editor, click Dashboard.
- Click Settings.
- Click Authentication.
- Click Set Up next to Single sign-on (SSO).
- In Select SSO provider, choose Microsoft Azure AD.
- Enter your Azure Application (client) ID, Client Secret, and Directory (tenant) ID.
-
Keep Scope as
openid email profile. - For Discovery Url, enter: https://login.microsoftonline.com/{TENANT_ID}/v2.0/.well-known/openid-configuration
- Click Enable SSO.
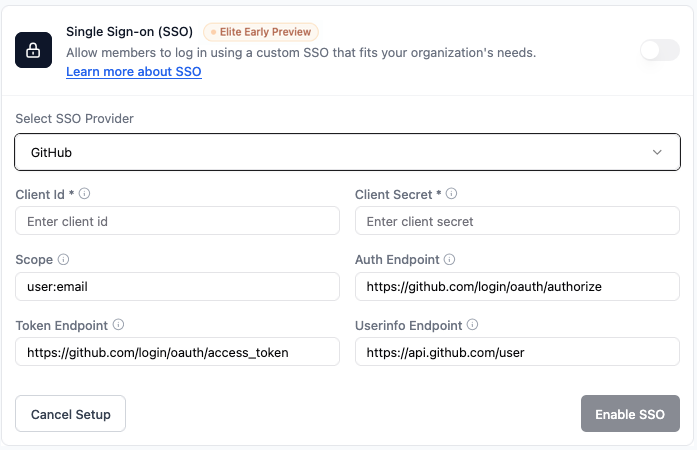
GitHub
Use a GitHub OAuth app as your SSO provider. Create an OAuth app in GitHub Developer Settings, then connect it in Base44. To set up GitHub SSO in Base44:- In your app editor, click Dashboard.
- Click Settings.
- Click Authentication.
- Click Set Up next to Single sign-on (SSO).
- In Select SSO provider, choose GitHub.
- Enter your GitHub Client Id and Client Secret.
- Keep Scope as
user:email. - Keep the default Auth Endpoint, Token Endpoint, and Userinfo Endpoint values for GitHub.
- Click Enable SSO.
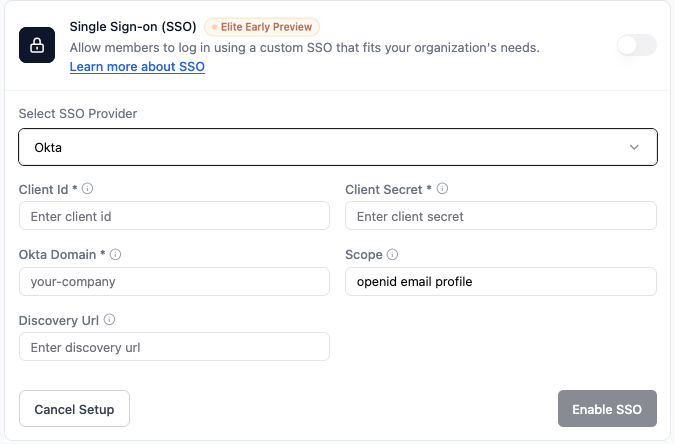
Okta
Use Okta as your SSO provider. In your Okta Admin Console, create an OIDC Web application for your Base44 app, then add the credentials in Base44. To set up Okta SSO in Base44:- In your app editor, click Dashboard.
- Click Settings.
- Click Authentication.
- Click Set Up next to Single sign-on (SSO).
- In Select SSO provider, choose Okta.
- Enter the following:
- Client Id: Your Okta client ID.
- Client Secret: Your Okta client secret.
- Okta Domain: Your Okta domain (e.g.
your-company.okta.com). - Scope: Keep
openid email profile. - Discovery Url: Your Okta discovery URL.
- Click Enable SSO.
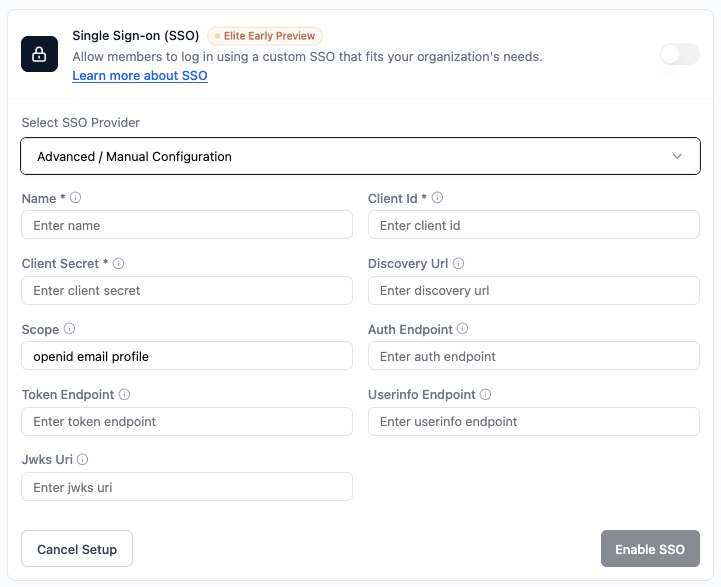
Advanced / Manual configuration
Use Advanced / Manual configuration to connect any OIDC compatible identity provider that is not covered by the built in options. This includes providers such as Kakao, as long as they support OIDC and you configure them with the correct details from your provider. To set up Advanced / Manual configuration in Base44:- In your app editor, click Dashboard.
- Click Settings.
- Click Authentication.
- Click Set Up next to Single sign-on (SSO).
- In Select SSO provider, choose Advanced / Manual Configuration.
- Fill in the following fields using your provider’s values:
- Name: A name for this SSO configuration (for example,
Auth0,Keycloak,Kakao, or your identity provider name). - Client Id: Your OIDC client ID.
- Client Secret: Your OIDC client secret.
- Scope: Keep
openid email profile. - Discovery Url: Your provider’s discovery URL, if available.
- Auth Endpoint, Token Endpoint, Userinfo Endpoint, Jwks Uri: If you are not using a discovery URL, paste each endpoint from your provider’s documentation.
- Name: A name for this SSO configuration (for example,
- Click Enable SSO.
Step 3 | Test your SSO login
After setting up SSO, test that everything works as expected. To test your SSO login:- Log out of your app if you are currently signed in.
- Go to your app’s login screen.
- Click Log in with SSO or select the provider you configured.
- Sign in using an email address from your approved domain.
FAQs
Click a question to learn more about SSO.Do I need to set up SSO if I only use one login?
Do I need to set up SSO if I only use one login?
No, SSO is optional. You can continue using your existing login method if it works for you. If you want your team to log in with Google, Microsoft, GitHub, Okta, or another OIDC provider, you can set up SSO and configure the provider you use.
What is a redirect URI and where do I use it?
What is a redirect URI and where do I use it?
A redirect URI tells your identity provider (like Google or Microsoft) where to send people after they log in. You enter it when you set up SSO in your provider’s dashboard. It should look like this:https://app.base44.com/api/apps/{{APP_ID}}/auth/sso/callback
Make sure to replace
{{APP_ID}} with your actual Base44 app ID.What is a discovery URL and do I need to add it?
What is a discovery URL and do I need to add it?
A discovery URL tells Base44 how to connect to your identity provider. It helps Base44 automatically find the right endpoints and configuration values. You only need this for some providers.
- For Google, you do not need to enter a discovery URL. Base44 handles it automatically.
- For Microsoft (Azure / Entra ID) and Okta, your provider gives you a discovery URL. Copy it into the Discovery Url field in your Base44 SSO settings.
- For GitHub, you can leave the discovery URL field blank.
- For Advanced / Manual providers such as Kakao, follow your provider’s documentation. If they give you a discovery URL, paste it into the Discovery Url field. If not, enter the individual endpoints instead.
If your provider gives you a discovery URL, paste it into the Discovery Url field in your Base44 SSO settings. If not, you can leave it empty and fill in the endpoints manually.
What if I see an error when logging in using SSO?
What if I see an error when logging in using SSO?
Check the following:
- Your redirect URI in Base44 exactly matches the one in your provider’s dashboard.
- Your client ID, client secret, and, if used, Discovery Url are correct.
- The scope is set as
openid email profilein both your provider’s configuration and in Base44 (or an equivalent email scope).
Why does the Google login still show "base44.com" instead of my app name after setting up custom SSO?
Why does the Google login still show "base44.com" instead of my app name after setting up custom SSO?
If Google still shows
base44.com as the app name or badge, your custom Google project has not been fully approved yet. Once Google approves your project, your app’s own name or branding will appear instead of base44.com.How can I make sure my app name appears in the Google login instead of "base44.com"?
How can I make sure my app name appears in the Google login instead of "base44.com"?
Finish setting up your custom SSO, publish your app, and submit your Google project for approval. After Google approves the project, your app name or branding will appear during sign-in instead of
base44.com.Which applications commonly use SSO or OAuth?
Which applications commonly use SSO or OAuth?
Many services support SSO or OAuth when working with enterprise or managed accounts, including: Langfuse, OpenAI, Anthropic, Mongo, Mixpanel, Mintlify, SendGrid, FeatureBase, Cloudflare, Logfire, GitHub, GCP, Render, AWS, Deno, Gong, Appspot, DocuSign, and Modal.

